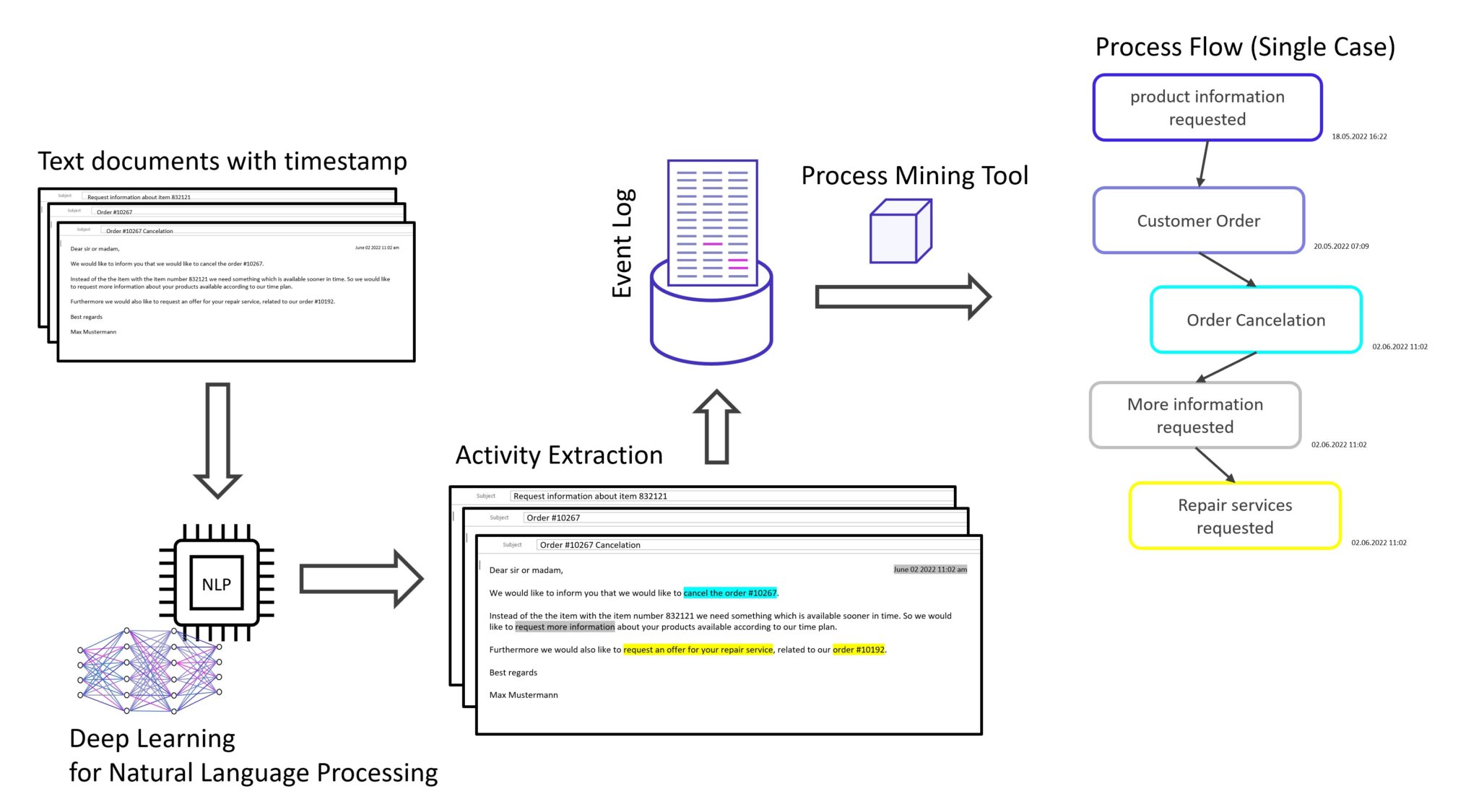
How unstructured data can be used for Process Mining
How unstructured data can be used for Process Mining with Deep Learning for Natural Language Processing and Computer Vision.

How unstructured data can be used for Process Mining with Deep Learning for Natural Language Processing and Computer Vision.
The DATANOMIQ AI Assessment is the check-up for your organization. We examine how your business organization can benefit from AI, with real results and implementation blueprints.
There are occasions when one or more serverless functions are not sufficient to represent a service. For these cases, there is Google Cloud Run on the Google Cloud Platform. Cloud…
Process Mining is a method of data analysis to data-driven audit, monitor or analyze process flows. See our Infographic how it works.
Nowadays, companies are not only evaluated according to their sales and profits, but also according to their data. Many organizations are far from satisfied with their data management, the business…
A fuzzy matching was used to combine the data from the two different sources. A selection of fuzzy string-matching algorithms was tested, for example Jaro-Winkler Distance, Levenshtein distance, Soundex or cosine similarity. The open-source algorithms can be very efficient and there is a selection to choose from depending on the use case.
Let’s say our customer needs structured, labeled images for an online tourism portal. The task for our AI model is therefore to recognize whether a picture is a bedroom, bathroom, spa area, restaurant, etc. Let’s take a look at the possible training methods.
How to protect the corporate identity of any company by ensuring consistent branding with automated font recognition using artificial intelligence (deep learning).
BI reporting has become an indispensable part of any company. In business intelligence, companies sometimes have to choose between tools such as PowerBI, QlikSense, Tableau, MikroStrategy, Looker or DataStudio (and…
Google, Amazon and Microsoft are the three big players in cloud computing. The cloud comes into question for almost all possible application scenarios, for example the hosting of company software,…